TL;DR
- V3 is near-ready. Following the whitepaper vision, the first production-ready Lido V3 build has run through two public testnets and is in late audits. Final testnet and follow-up changes from the audits are still to come.
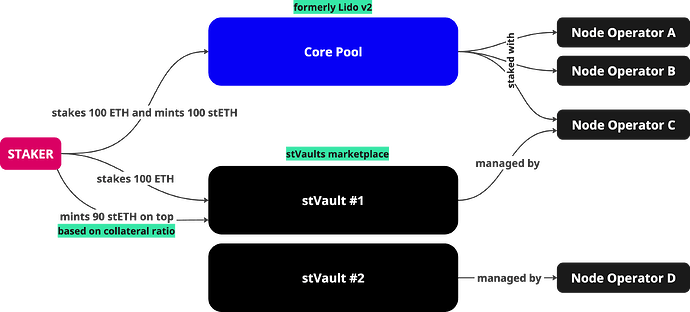
- stVaults introduce a non-custodial, over-collateralized way to choose how and with whom to stake while still minting stETH. The existing 1:1 staking path continues as the Core Pool.
- Why it matters. V3 turns the Lido protocol from a single pool into Ethereum staking infrastructure: operator-led vaults, DVT/restaking sidecars, leverage loops, and institutional setups.
- Safety first. stETH minting via stVaults rolls out in phases with global and per-operator caps, backed by a published risk assessment framework for stVaults.
- Ask. Lido contributors are seeking DAO feedback and sentiment ahead of Snapshot and, if supported, an on-chain Aragon vote after testnets, audits, and final security checks conclude.
Intro
Lido V3 originated in GOOSE-2 to broaden stETH’s product surface. Since then: early-adopter program, public RFCs, multiple private devnets, two public testnets on Hoodi, and a multi-firm audits campaign (pending completion).
Key milestones:
- Feb 2025: Initial V3 reveal + early-adopter program
- Apr 2025: Testnet-1 (Hoodi), Risk Assessment framework for stVaults published, stVaults fees approach
- May 2025: Whitepaper RFC posted
- Jun 2025: Testnet-2 (Hoodi) + Audits kick-off
- Aug 2025: Default risk assessment framework and fees parameters for Lido V3 (stVaults)
- Sep 2025: stVaults Committee proposal, Whitepaper RFC wrap-up; deployment lookahead planning
With design converged and audits maturing, now is the right time to gauge DAO alignment on upgrading to V3.
Design
V3 101: What is Lido V3? (Recap)
stVaults are isolated within the normal operation mode defined by the risk assessment framework for stVaults. They are opt-in vault contracts that delegate stake to a chosen operator under configurable terms (fees, MEV/sidecars, key management, insurance). They’re non-custodial and connect to Lido’s liquidity layer by over-collateralized stETH minting (a reserve stays in ETH to absorb penalties). Vaults can later be disconnected and ossify their implementation, removing any future DAO-imposed changes.
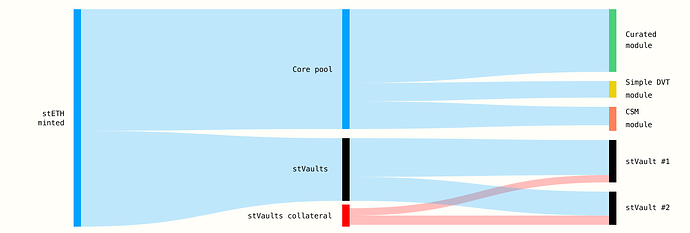
Core Pool (formerly Lido V2) remains unchanged. Users who want simple 1:1 battle-tested staking keep the same path. V3 = Core Pool + stVaults. The same stETH token is used across both paths; oracle/accounting was upgraded accordingly.
What this unlocks (live examples)
- Operator-led liquid staking: stake directly with a preferred operator and still get stETH.
- Custom strategies: DVT clusters, restaking sidecars, specialized MEV/infra.
- DeFi loops: use stETH as collateral while ETH keeps compounding in-vault.
- Institutional vaults: bespoke terms without sacrificing liquidity.
Motivation
V3 resolves the staking setup control vs liquidity trade-off. Today, many stakers want operator choice, DVT, or compliance requirements — features that a single pooled model can’t serve well. V3 decouples validator selection from the liquidity layer, expanding stETH’s addressable market while improving validator set diversity and resilience.
Strategically, V3 delivers on GOOSE-2: Lido evolves from “the pool” to a platform others can build on, supporting a diverse product line. It aligns incentives: operators win direct demand; builders compose new products; stakers gain choice without losing liquidity. Vault isolation and opt-out mechanics mitigate the risk of DAO-imposed upgrades without a vault owner’s consent, ensuring vault sovereignty and an effective escape hatch.
Foundations and in-depth design
For those interested in diving deeper, here are key reference materials that underpin the Lido V3 design and plan:
- Lido V3 Whitepaper (Final Draft) – Comprehensive overview of the V3 architecture, stVault mechanics, and design rationale.
- User and integration guides — Hands-on docs and recipes to build atop of Lido V3.
- Lido Staking Vaults: Technical Design and Architecture - The living document, outlining the core stVaults design principles, architecture, and mechanics at a high level.
- Lido Improvement Proposals - A set of design documents describing important Lido protocol and governance mechanisms aspects, together with their cornerstone changes brought with the Lido V3 upgrade.
- LIP-31: Expanding stETH liquidity layer with over-collateralized minting - Introduces the over-collateralized accounting system enabling stETH to be backed by ether outside the Lido Core pool. Defines the VaultHub registry, external shares mint/burn mechanics, and reserve requirements.
- LIP-32: Sanity checks for stVaults - Describes the comprehensive sanity checks including quarantine periods for suspicious value increases using the “lazy oracle” mechanism.
- Risk Assessment Framework for stVaults – A forum post outlining the risk management model for V3. It covers the guiding principles (e.g. stVault users don’t negatively affect stETH holders), defines the global cap on stVault usage (initially ~30% of Lido’s TVL, ~3M ETH), and describes how Reserve Ratios and per-vault caps are set to contain slashing risks and maintain stETH redeemability. This framework informed the secure rollout limits below.
- stVaults committee - A forum proposal to establish a committee, monitoring stVaults’ performance and evolution, facilitating onboarding of new stVaults, and handling requests from stVault Owners and Node Operators for non-default terms.
- stVaults Fees Approach – Discussion of the fee model for stVaults. Lido V3 introduces up to three types of fees on vaults (infrastructure fee, reservation liquidity fee, and liquidity fee) to ensure the DAO can fairly charge for use of the system’s resources. The fee approach is flexible to accommodate different use cases (e.g. institutions might accept higher infra fees but need low liquidity fees). The final proposed default fee percentages and their basis are summarized in an update post (August 2025) after community feedback.
- Default risk assessment framework and fees parameters for Lido V3 (stVaults) - A forum thread, unveiling the set of default parameters that will be proposed for stVaults for risk framework and default fee values.
- Lido V3 Audit scope – An audit scope, describing related to Lido V3 components (solidity contracts and off-chain oracles) and important design aspects for security experts consideration.
Implementation
Current status
- Code: feature-complete; offchain stVaults-enabled oracle and accounting rewrites to scale operator count and track vault paths.
- Audits: To ensure security, Lido V3 has been undergoing extensive audits by multiple independent firms (each focusing on different aspects):
- Certora: formal verification + on/off-chain review
- ConsenSys Diligence: deep on-chain review + invariant fuzzing
- Composable Security: oracle/infra, threat models
- MixBytes: vault logic, global accounting math, governance wiring
As of this writing, several interim audit reports have already been delivered, with all audits being targeted to conclude by mid-October 2025.
- Testing: two public testnets and multiple internal devnets so far; the final public testnet to be launched in October
- Bug bounty: to be extended on Immunefi post-audit hardening
Rollout plan
Secure Rollout with Phased Caps
While anyone can create a vault and stake ETH from day one, stETH minting through stVaults will be phased to limit risk and validate the system in live conditions.
Governance and oversight of the phases are split between:
- Lido DAO — explicitly decides on phase 1→2 transition via an on-chain vote (by adjusting the global minting cap).
- stVault Committee — monitors performance, operator behavior, and risk metrics; manages parameters (reserve ratios, per-operator caps, minting permissions, fees). It can propose forced exits and adjustments via Easy Track, subject to LDO veto.
The rollout follows a three-phase framework, gradually increasing scale and openness:
-
Phase 1: Pilot (starts with Lido V3 upgrade enacted)
- Global cap: 3% TVL (~300k stETH) total minted through stVaults
- stETH minting: permissioned node operators only (early adopters prioritized)
- Per-operator cap: 50k stETH, expandable if global cap not filled
- Permissionless vaults: staking enabled, minting disabled
-
Phase 2: Controlled Expansion (30 days with zero incidents related to stVaults + next DAO voting slot)
- Global cap: 30% TVL (~3M stETH) total minted through stVaults
- Identified operators: 50k cap, expandable on business-case review
- Permissionless vaults: staking enabled, minting disabled
-
Phase 3: Permissionless Mode (30 days with zero incidents related to stVaults + non-objected Easy Track motions)
- Global cap: same as Phase 2
- stETH minting: enabled for all vaults according to risk framework parameters
- Per-operator cap: up to 1M stETH (both identified and permissionless)
This phased rollout limits systemic risk, builds real-world data, and ensures stability before full-scale adoption.
Security considerations and emergency mechanisms
The protocol implements multiple layers of caps, limits, and pause mechanisms to ensure system safety:
1. Minting Caps and Limits
- Global external ratio cap: Enforces maximum percentage of stETH that can be minted through vaults (e.g., 3% in Phase 1, 30% in Phase 2)
- Global staking rate limit: All stETH minting (Core Pool + vaults) is subject to a 150k stETH/day moving window limit
- Per-vault share limit: Each vault has an individual limit, restricting the maximum stETH shares it can mint (derived from the risk tier assigned by default)
2. Pause and controls
- Lido DAO Agent can upgrade
VaultHubandStakingVaultbeacon proxy implementations (except for ossified stVaults), perform technical administrative actions, and assign/resign committees below. - stVaults Committee can initiate Easy Track governance motions related to risk framework parameters and corrective actions for individual vaults; the committee will be assigned by a dedicated proposal.
- GateSeal Committee: can push a time-limited emergency pause over VaultHub and Predeposit Guarantee (PDG) operations; it is proposed that the existing committee be used.
- Vault Owners:
- can manually pause beacon chain deposits
- can voluntarily disconnect a vault from the Lido protocol (the vault becomes detached from VaultHub and Oracle)
- being disconnected, can ossify its proxy implementation (excluding dependency on the Lido DAO governance)
3. Risk Thresholds
- Reserve Ratio (RR): Minimum reserve percentage (e.g., 10%) - blocks new mints when breached
- Force Rebalance Threshold (FRT): Critical reserve level (e.g., 5%) - enables forced rebalancing
- Bad Debt: When
vault.liabilityShares > stETH.getSharesByPooledEth(vault.totalValue()), vault enters the bad debt state
Note: as described in the failure modes of LIP-31, the bad debt losses can potentially be covered by:
- replenishing the staking vaults accrued bad debt with additional funds;
- socializing the bad debt among vaults containing slashed validators of the same node operator;
- executing a self-coverage application (see LIP-18);
- internalizing the losses to protocol, decreasing stETH token rebase (as it would have been with the Lido Core pool staking penalties) within the next oracle report (using the bad debt internalization mechanism)
These mechanisms work together to limit risks while allowing the protocol to scale safely. Emergency responses can be triggered at multiple levels - from individual vault issues to system-wide concerns.
Next steps
We invite the community to provide feedback on this proposal and the Lido V3 design. Please share any concerns, questions, or suggestions you have here in this forum thread. Assuming general support and no blocking issues are raised, the tentative plan is to proceed with a Snapshot vote to signal DAO approval of the V3 upgrade.
Tentative timeline
- Late Sep 2025: Barring objections, initiate a Snapshot vote for signaling support of Lido V3.
- Oct 2025:
- If Snapshot support is positive, deploy the Lido V3 contracts to the Hoodi testnet, upgrading the main Lido testnet instance.
- Finalize all ongoing audits, address fixes, and complete minor contract changes. A summary of audit results will be published in the thread for DAO review, assuming no pending resolution findings are left.
- Schedule an on-chain vote to upgrade and execute the contract changes. The exact details (specific contract addresses, etc.) will be posted before the vote, together with 3rd-party deployment verification notes.
- Nov 2025: Enactment of Lido V3 upgrade on mainnet, assuming the on-chain vote passes. Contracts will be upgraded, and the new modules (VaultHub, etc.) will be initialized. Phase 1: Pilot begins immediately at this point – all vaults can start accepting deposits, and eligible ones can access minting within the 3% global cap. Close monitoring in the initial weeks post-launch.
- Mid-Dec 2025: If everything runs smoothly, transition to Phase 2: Controlled Expansion. This would involve lifting the global cap to ~30% via a new DAO vote. Additional node operators and stVaults might be invited to enable minting, possibly in batches. Also, per-node operator minting limits increases expected according to the demand.
- ~Q1 2026: Target for Phase 3: Permissionless Mode activation. By this time, we expect to open stVaults minting to the public. Once enabled, any new vault that connects to the Lido protocol can permissionlessly mint stETH up to its tier limits.
Note: timing remains subject to security and operational readiness.
Thanks to everyone who has been reviewing, testing, and pressure-testing V3; let’s keep building on Ethereum and Lido <3.